Jenna Beshara | Katelyn O’Connor | Leon Tang

An Exploration of the Natural World Through Art: Series of Landscape Paintings Made with all Natural Pigments
Jenna Beshara
Lee Boot, Visual Arts
Locations:
- Exhibit: Paintings will be on display in the UC Lobby all day.
- Oral Presentation: UC 312, 2:15 – 2:30 p.m.
Is it possible to make paintings in a traditional manner using a non-traditional medium that better serves environmental concerns than current products sold? My goal is to make a series of landscape paintings all made by natural, foraged goods and turpentine oil, and showcase the paintings as well as the paint-making process. I went abroad for the first time last year to Wales, and the way Welsh culture is deeply integrated into the natural world has guided my art and art process ever since. Acrylic paint is made from plastic, and oil paint can have toxic chemicals, like mercury, that is harmful to the environment. I find it hypocritical that one can be a landscape artist and use these paints, so I’d like to research and experiment with creating my own natural pigment, and mixing those pigments with linseed oil. This series is, at the heart of it, a love letter to the environment, as I find something poetic about making a series of landscape paintings used by natural, foraged ingredients. Additionally, it reflects what I’ve learned in my time abroad, and the respect and connection I gained for the environment and an environment-centered approach to art.
Dance As Language: A Choreographic Exploration of the Interpretation of Idiomatic Phrases in the English Language
Katelyn O’Connor, Dances
Mentor: Ann Sofie Clemmensen, Dance
Locations: UC 312 1:35 – 1:50 p.m.

This research addressed an interpretation of English idioms on a literal to figurative scale, with the presentation being dance performance. The motivation for this research stemmed from interacting with a variety of people with English as their second (or non-primary) language. There are an estimated 25,000 idioms in the English language, and while there are idioms in other languages as well, research has shown it is not nearly as extensive as in the English language. Through personal interpretations, surveys collected from over seventy native and non-native English-speaking adults, and in-depth choreographic exploration, this research showed that there is a large depth of interpretations when it comes to English idioms, ranging from extreme ends of the scale of literal to figurative. The final presentation included an exploration of body, object, and space, utilizing props and movement in tandem to convey the tension between the literal and figurative language.
This work was funded, in part, through an Undergraduate Research Award from the UMBC Division of Undergraduate Academic Affairs.
A survey of Deceptive Techniques in Mobile Autonomous Systems: Attacks and Defense
Leon Tang, Information Systems
Mentor: Zhiyuan Chen, Information Systems
Locations: UC Ballroom 10 – 11:30 a.m.
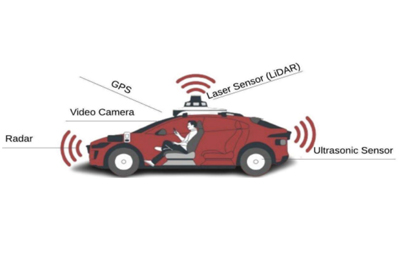
Mobile Autonomous Systems refer to robots, ground vehicles, drones etc. that can move autonomously. Such a system relies on sensors such as cameras and GPS to learn the states of the system itself as well as its surroundings and often machine learning (such as computer vision) and AI for autonomous decision making (e.g., to navigate). Deception is a serious threat to securing such systems because both the input to sensors as well as the machine learning models used in decision making can be misled by injected deceptive information. This project conducts a comprehensive survey of existing deception-based attacks against mobile autonomous systems and identifies gaps in the existing research. Compared to existing surveys, our survey considers various degrees of sophistication of the attacking strategies and type of data being altered. Our work also identifies gaps of existing research such as relatively little work has been done on multi-stage attacks and attacks that influence long term decision making. Our work can be used to help better understand deception based attacks as well as developing better defense strategies.